Video Demonstration: Hacking WEP
This is a tutorial on how to crack Wired Equivalent Privacy (WEP), whether it is 64-bit or 128-bit. Depending on whether there are clients connected to your Access Point (AP) or not will decide which method you need to use to generate wireless traffic. If you are looking for a Linux Distribution that contains all of the tools needed for this, I would highly recommend Back|Track 2. Not only does it contain hundreds of open source tools, but it is also based on the Slax Live CD, which has excellent modularity. To sniff for wireless networks and capture packets you can use a variety of different applications, but the most widely used are Airodump and Kismet. I would suggest using Airodump since it comes in the Aircrack Suite and is what I will be using in this tutorial.
I will describe two different methods of generating wireless traffic. The first assumes that there is at least one client connected to the AP and the second assumes that there are no clients connected to the AP. The first method works by capturing a packet that is being sent from the client you are sniffing traffic from to the AP. Your machine will then send that packet to the AP hundreds of times a second in order to rapidly generate wireless traffic. The packet that you sniff must have an Initialization Vector (IV) at the beginning of the packet, which is a 24-bit block that initializes the encryption. The second method works by sending fake authentication packets to the AP every thirty seconds. Once you are authenticated, you then send Address Resolution Protocol (ARP) requests to the AP hundreds of times a second while deauthenticating and reauthenticating yourself.
Now, let us get started. I’m going to assume that you have a laptop or desktop with a wireless card capable of injecting packets and have Back|Track 2 running. Enter in your user as root with the password toor. Then run xconf to configure the Graphical User Interface (GUI) for your video card and startx to start KDE. Once you are in KDE, open a console and enter in iwconfig to make sure that Back|Track 2 has detected your wireless card. The output will vary depending on your wireless card and driver. My output is as follows:
lo no wireless extensions.
eth0 no wireless extensions.
ath0 IEEE 802.11g ESSID:”Linksys”
Mode:Managed Frequency:2.442 GHz Access Point: 00:06:25:9A:50:C8
Bit Rate:54 Mb/s Tx-Power:18 dBm Sensitivity=187/255
Retry min limit:7 RTS thr:off
Power Management:off
Link Quality=54/100 Signal level=39/100 Noise level=1/100
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:0 Missed beacon:0
sit0 no wireless extensions.
If Back|Track 2 did not detect your wireless card you may try loading different drivers or manually downloading and installing them yourself. Now let us set our wireless card to Monitor mode, which will enable us to discover Access Points, sniff wireless traffic, and inject packets. Depending on your wireless card and driver you may have to use either the first set or second set of commands. Also, throughout the tutorial you may have to change the wireless interface in the commands, such as ath0 to wlan0, and so on. The commands are as follows:
ifconfig ath0 down
iwconfig ath0 mode monitor channel 6
ifconfig ath0 up
– or –
ifconfig ath0 down
wlanconfig ath0 destroy
wlanconfig ath0 create wlandev wifi0 wlanmode monitor
ifconfig ath0 up
Now that your wireless card is set to Monitor mode we can start Airodump. Airodump will allow us to sniff wireless traffic and log it to a file, which we will later run through Aircrack. The following command will start Airodump on channel six, write the captured packets to output-01.ivs, and run on the wireless interface ath0. If you would prefer to scan all channels and all frequencies, you can add the --abg option into the command before the wireless interface. If you do opt to do to that, be sure to exit Airodump once you have found the channel the AP is on. Run Airodump again and set the channel to that of the AP, this way the AP stays on that frequency. The command is as follows:
airodump-ng –channel 6 –write output –ivs ath0
Now that Airodump is running on that console we need to open a new tab or console. Once that is done we will start Aireplay, which is also a tool found in the Aircrack Suite. This is the point where you must use either the first or second method. If the AP has at least one client connected, use the first method. If the first method does not work or there are no clients connected to the AP, use the second method.
First Method:
If the AP has at least one client connected, you want to use this method. The following command will send five-hundred and twelve packets every second from the clients Media Access Control (MAC) Address of 00:06:25:B3:D6:E2 to the AP with the MAC Address of 00:06:25:9A:50:C8 on the wireless interface ath0. Since the captured packet has the IV at the beginning and Aireplay is sending the packet to the AP with the clients MAC Address, the AP will allow the traffic to be passed through. Edit the AP MAC Address, client MAC Address, and wireless interface to suite your needs. The command is as follows:
aireplay-ng –interactive -b 00:06:25:9A:50:C8 -h 00:06:25:B3:D6:E2 -x 512 ath0
Once Aireplay successfully finds a packet it will prompt you to either use that packet or search for a new packet. If the packets source is the Broadcast Address or the clients MAC Address and the destination is the AP, odds are it will work. You may have to try many packets before you find one that generates wireless traffic, but eventually you should find one. That’s all for the first method. If Airodump is rapidly capturing data then you may move on to the Aircrack portion of this tutorial. Once again, if the first method did not work then you may try the second method, but you have a better chance of success if there is at least one client connected.
Second Method:
If the first method does not work or there are no clients connected to the AP, you want to use this method. The first command will fake authenticate every thirty seconds using the fake client MAC Address 00:06:25:C1:E5:37 to the AP with the MAC Address of 00:06:25:9A:50:C8 and Service Set Identifier (SSID) of Linksys on the wireless interface ath0. Edit the SSID, AP MAC Address, fake client MAC Address, and wireless interface to suit your needs. The list of commands must be run in order for them to work properly. The first command is as follows:
aireplay-ng –fakeauth 30 -e Linksys -a 00:06:25:9A:50:C8 -h 00:06:25:C1:E5:37 ath0
The second command will send five-hundred and twelve ARP requests every second using the fake client MAC Address of 00:06:25:C1:E5:37 to the AP with the MAC Address of 00:06:25:9A:50:C8 on the wireless interface ath0. The second command is as follows:
aireplay-ng –arpreplay -b 00:06:25:9A:50:C8 -h 00:06:25:C1:E5:37 -x 512 ath0
The third command will send five deauthentication packets using the fake client MAC Address of 00:06:25:C1:E5:37 to the AP with the MAC Address of 00:06:25:9A:50:C8 on the wireless interface ath0. The third command is as follows:
aireplay-ng –deauth 5 -a 00:06:25:9A:50:C8 -c 00:06:25:C1:E5:37 ath0
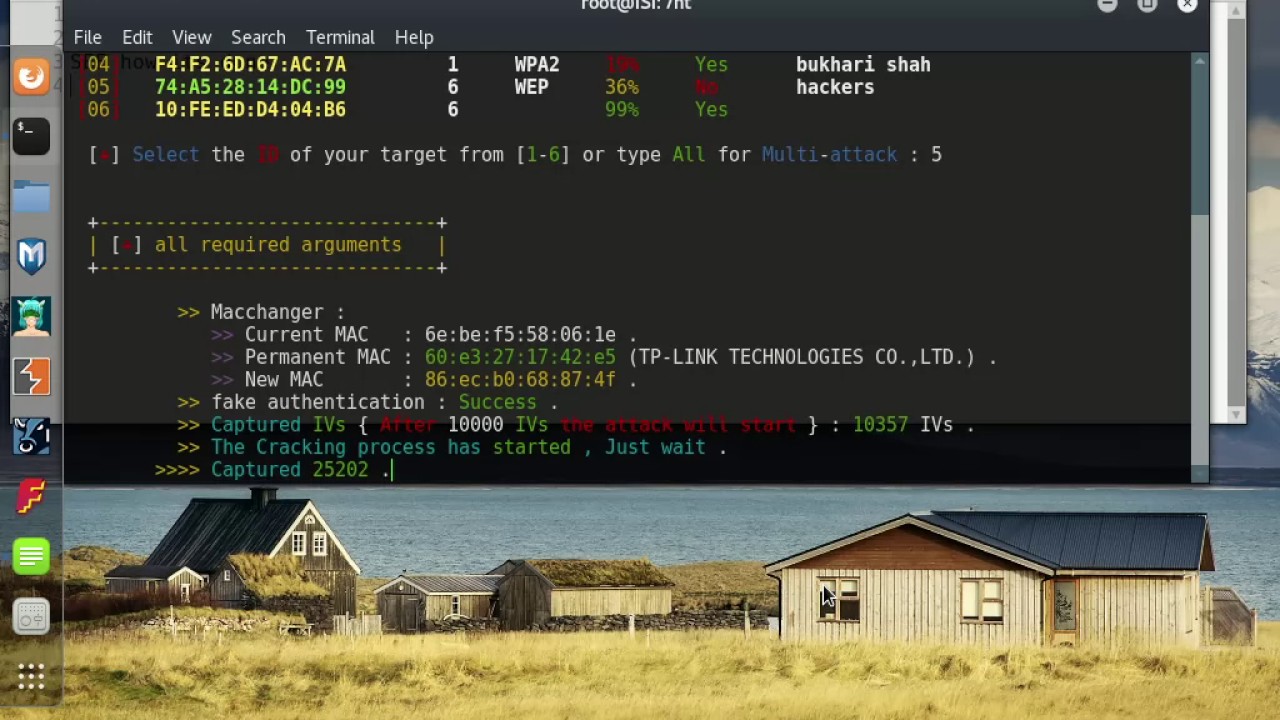
From this point on it does not matter which method you used to generate wireless traffic, as long as the data is rapidly increasing in Airodump. Usually a 64-bit WEP key can be brute forced with about 250,000 packets of data and a 128-bit WEP key can be brute forced with about 500,000 packets of data. Now that we have Airodump capturing wireless packets and Aireplay generating wireless traffic, we can start Aircrackto begin the process of brute forcing the WEP key. The following command will run Aircrack on output-01.ivs and search for the AP MAC Address of 00:06:25:9A:50:C8 using the default fudge factor of two. When we ran Airodump, we set the filename as output.ivs, but because Airodump automatically increments the filename, it will start off as output-01.ivs and so on. A couple of other options are -f for the fudge factor or -n for the WEP key length. The fudge factor will increase or decrease how thorough the brute force is, but the higher fudge factor the longer it takes. The default fudge factor is two, but if you have a sufficient amount of data captured, such as 750,000 packets, and the WEP key is still not cracked after a few minutes then you may want to up the fudge factor to four or run two instances of Aircrack using different fudge factors. Usually you do not have to set the WEP key length, but if you do happen to know it then setting it may speed up the brute force. The most common WEP key lengths will be 64-bit or 128-bit. The command is as follows:
aircrack-ng -b 00:06:25:9A:50:C8 output-01.ivs
Once Airodump has captured enough data and Aircrack has brute forced the key, Aircrack will state Key Found and display the WEP key. The time it will take Aircrack to brute force the WEP key depends on the WEP key length, how much data was captured, and the processing power of your laptop or desktop. I have had times where I captured over one million packets and ran two instances of Aircrack using fudge factors of two and four, but it still took thirty minutes to brute force the key. Then again, i have had times where i captured less than 200,000 packets and brute forced the WEP key in under five minutes. The average time it should take to brute force an average WEP key should be about ten to fifteen minutes. My Aircrack output is as follows:
Key Found! [ 40:39:19:87:08 ]
Now we must connect to the AP using the supplied WEP key. The following commands will set your wireless card to Managed mode, connect to an AP with the SSID of Linksys, use channel six, and 40:39:19:87:08 as the WEP key. Once again depending on your wireless card and driver you may have to use either the first set or second set of commands. Also, if you would like to connect to the AP from Windows you must take out the colons in the WEP key. The commands are as follows:
ifconfig ath0 down
iwconfig ath0 mode managed essid Linksys channel 6 key 40:39:19:87:08
ifconfig ath0 up
– or –
ifconfig ath0 down
wlanconfig ath0 destroy
wlanconfig ath0 create wlandev wifi0 wlanmode sta
iwconfig ath0 essid Linksys channel 6 key 40:39:19:87:08
ifconfig ath0 up
Now we should be connected to the AP, but we need to be assigned an Internet Protocol (IP) Address. We will use the Dynamic Host Configuration Protocol (DHCP) to be leased an IP Address with a Domain Name System (DNS) Server. The following command will run the DHCP Client on the wireless interface ath0. The command is as follows:
dhcpcd ath0
If the AP or Router is not running DHCP we can manually set the IP Address, Subnet Mask, Default Gateway, and DNS Server. The following commands will assign the wireless interface ath0 an IP Address of 192.168.1.105, with a Subnet Mask of 255.255.255.0, a Default Gateway of 192.168.1.1, and write the DNS Server 4.2.2.1 to /etc/resolv.conf. The commands are as follows:
ifconfig ath0 down
ifconfig ath0 192.168.1.105 netmask 255.255.255.0
ifconfig ath0 up
route add default gw 192.168.1.1 ath0
echo nameserver 4.2.2.1 > /etc/resolv.conf
Finally, we test our connectivity to make sure that we are successfully connected to the AP and Internet. The command is as follows:
ping cyber-knowledge.net
The output of that command should be as follows:
PING cyber-knowledge.net (66.79.165.146) 56(84) bytes of data.
64 bytes from techreads.cyber-knowledge.net (66.79.165.146): icmp_seq=1 ttl=48 time=78.6 ms
64 bytes from techreads.cyber-knowledge.net (66.79.165.146): icmp_seq=2 ttl=48 time=77.6 ms
64 bytes from techreads.cyber-knowledge.net (66.79.165.146): icmp_seq=3 ttl=48 time=77.6 ms
— cyber-knowledge.net ping statistics —
3 packets transmitted, 3 received, 0% packet loss, time 2014ms
If everything went as planned then you should be connected to the AP and Internet. After that it is up to you to decide what you want to do, but I would suggest running Nmap to discover what is on the network. If you would like to view a video demonstration of this tutorial you can find it here. Also, if you do use this tutorial, please comment on how your experience with it went. Have a great time and remember, be responsible.
Resources:
Hacking WEP
Aircrack Suite
Back|Track 2
Kismet
Nmap
Slax Live CD
